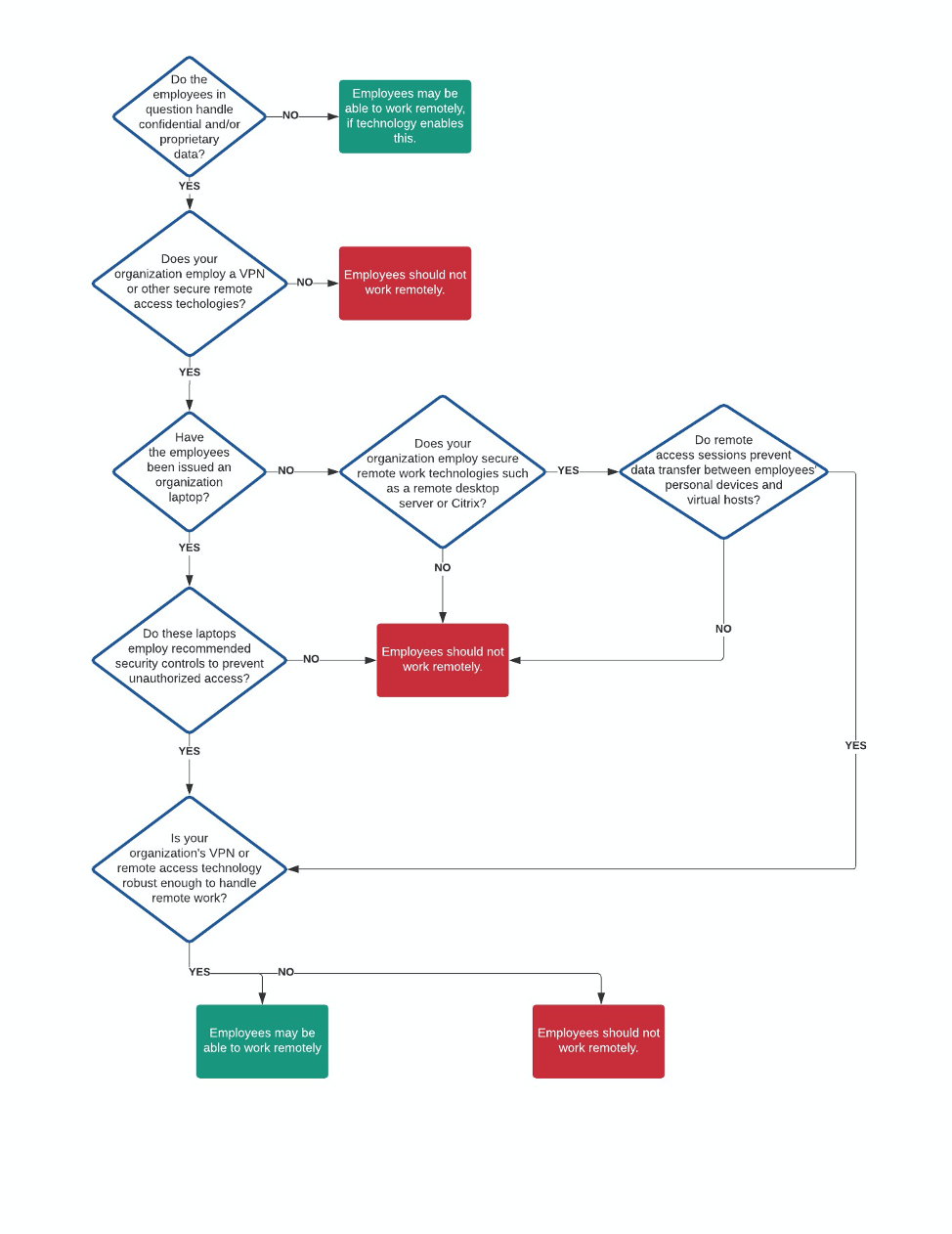
By Luke WilladsenAs many organizations move to a remote-work posture due to the rapid spread of COVID-19, it’s important that those responsible for IT and IT security can ensure their organization’s remote work policies and technologies are securely implemented and capable. No two organizations are alike, and exact security requirements are unique to your organization. The bottom line is that remote work technologies and policies should be designed to prevent unauthorized access to your network, systems, and confidential and/ or proprietary data. There is no one-size-fits-all approach to this, organizations must develop a true understanding of their threat profile to better determine which security controls are right for them. To accomplish this, it’s important to ask the right questions:
This blog post specifically focuses on answering the last question. There are multiple solutions for implementing remote work technologies and policies, and it is possible to be budget-conscious while also ensuring that remote access is secure. You will have to make the choices that are right for your organization. EmberSec suggests taking one of these two routes to achieve secure remote access for employees:
Before diving into proper implementation, it’s important to recognize that many employees at many organizations do not work with confidential or proprietary information. If these employees can perform their work tasks remotely, then it’s generally safe; just ensure that these employees are isolated from systems and network segments that could encounter confidential and/or proprietary information and are educated on current policies and expectations. Secure VPN Use Let’s dig into option number one – the use of a VPN for remote work. If confidential or proprietary data is involved, or if employees must interact with critical systems and/or networks, these employees should never be connecting into company networks from personal devices. These devices could be infected with malware and introduce it into your greater organizational network. CAVEAT: if there is no requirement for employees to access confidential or proprietary information, then it might be safe for employees to connect to the VPN, but they must land in a secure enclave of the network. It may be better to let these employees rely on cloud services and skip connecting to the VPN altogether. If employees work with confidential or proprietary information, or they interact with business-critical systems, their origination system (when connecting to the VPN) needs to be an organization-managed system such as a company laptop or desktop. There are essential reasons why this is important. An organization-managed system allows for necessary control over the device, allowing your system administrators to:
With full configuration management over the devices that are authorized to connect into the network, organizations can ensure they have taken strong precautions before allowing users to connect into their network and access confidential or proprietary information. Now let’s get into the VPN configuration. It’s just as important for organizations to properly implement their VPN solution. Multi-factor authentication (MFA) for your VPN(s) is crucial and should NOT be optional. MFA is arguably the most effective security control you can use to prevent unauthorized access and increases the difficulty for adversaries to achieve a breach by several factors. Second, you should ensure that VPN clients land in a secure network enclave. The secure VPN client enclave should have granular firewall rules that dictate exactly which hosts and ports VPN clients can communicate over. Employ the principle of least privilege when determining firewall rules. Finally, find a way to ensure that organization-owned devices are the only devices allowed to connect into the VPN. This is hard to do, and you may have to get creative to accomplish this. The use of client certificates that are locked down and cannot be exported from the organization-owned device is one solution. Remote (and Virtual) Desktop Technologies One alternative to VPN use over secure organization-managed systems are remote desktop technologies like Microsoft’s Remote Desktop Services (RDS), and virtualized desktop technologies like Citrix, Hyper-V, VirtualBox, and VMware Horizon. Rather than connecting a device into your organization’s network as a host, you can allow users to connect into hosts that are already in your environment. There are pros and cons to this option, as there are with using a VPN. With the right security controls implemented, remote desktop technologies can be made to be secure, and you’ll find that many of the same security controls apply to both options I’m discussing in this blog. In addition to standard security measures (ex. endpoint security, EDR, firewalls, whitelisting, mandatory updates, group policy configuration), there are two security controls that are crucial when using remote and virtual desktop technology for remote work:
Stress-Testing If you’re going with either of the options I’ve presented, it’s crucial that your infrastructure can handle the load of implementing a remote work policy during these trying times. If the infrastructure isn’t robust enough, you’re going to have big problems. If you lack the proper bandwidth and are allowing all your employees to connect via your VPN, the network connection could be frustratingly slow and heavily impact the productivity of your employees. If the systems hosting your remote or virtual desktop services lack the required computing power, your users’ interactive sessions could slow to a crawl, preventing them from getting any work done. You need to stress test your remote work technologies to ensure they can handle the load. If your VPN has only ever had 50 concurrent users, what makes you think it can handle 1000? Conclusion Is your organization ready for a 100% remote work policy? If so, count yourself lucky. With the rapid spread of COVID-19 and ensuing global panic, many organizations aren’t ready and may attempt to implement such a policy anyway for fear of lost productivity. Implementing a 100% remote work policy without being properly prepared could do more harm than good for your organization, as it could result in a breach or outages. I hope this blog is helpful in enabling you to facilitate safe and secure remote work. Things We Didn’t Talk About This blog didn’t cover everything under the sun. We haven’t talked about any mobile applications that many organizations use, such as Outlook, Slack, Teams, and many more. We often discuss confidential information over email and other collaboration tools, and many of our organizations allow us to access to these platforms on our mobile devices. We also haven’t talked about externally hosted applications that many of our organizations use, such as Slack, Teams, GitHub, Salesforce, Confluence, Jira, and many more. Without employing certain security controls, these applications can be accessed from any system. Stay tuned for a future blog post on these topics! Anecdotal Misconfigurations I’ve Observed As a penetration tester, my job is to find security holes in the technologies implemented by my organization’s clients. Below are a few misconfigurations that I’ve observed in past remote work technology implementations.
Comments are closed.
|
|
© 2020 By Light Professional IT Services LLC. All Rights Reserved.
|

 RSS Feed
RSS Feed
