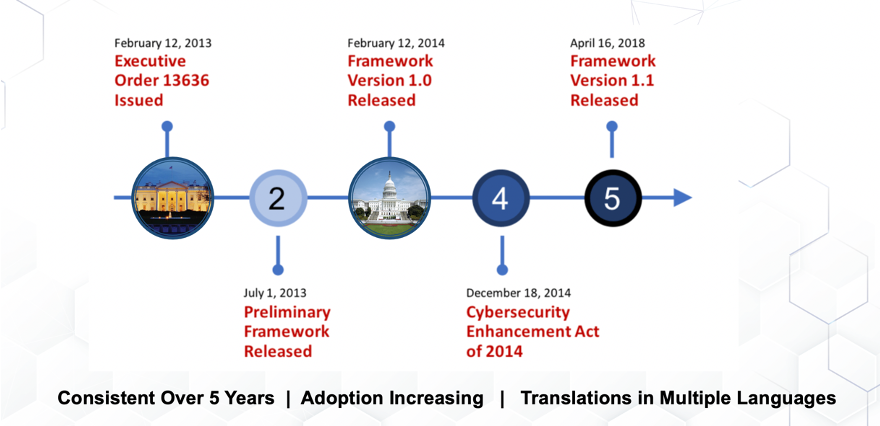
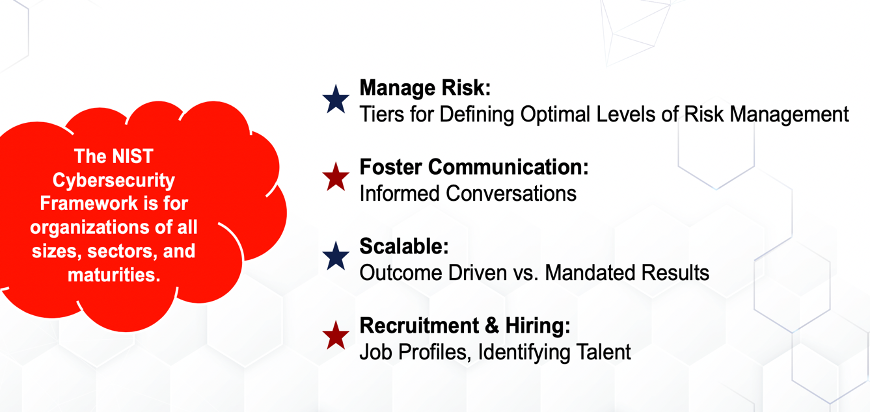
By Bradley WolfendenFor the majority of organizations, regardless of size, any mention of the word ‘cybersecurity’ can lead to some serious anxiety. Whether that anxiety is the result of a lack of general awareness, limited internal expertise, absence of a response plan, restricted budgets, or a myriad of other triggers, there is no doubt that the complex web of cyber best practices can be daunting. To help calm this overwhelming reality, many business leaders will turn to one of several existing cybersecurity frameworks as a starting place. These frameworks provide guidance around managing risk, foster improved communications, allow for scalability in application, and can support recruitment and hiring of cyber talent. For this blog post the EmberSec team digs in on the NIST Cybersecurity Framework to share how it can be leveraged to improve your overall cybersecurity strategy. We chose to focus this blog specifically on the NIST Framework due to our D.o.D. and government heritage, rich experience working with it, and due cause how it takes a threat-based approach to cybersecurity. The NIST Cybersecurity Framework: A History Since the publication of the Preliminary Framework was released in 2013, several iterations and revisions have been made available by NIST to better reflect the constantly evolving nature of cybersecurity, developments in technology, the emergence of new industry sectors, the state of adversaries, and the needs of its user base. Because of the NIST Cybersecurity Framework’s inherent flexibility and versatility, and evolution of the framework, adoption of the Framework both domestically and internationally has grown. Why Adopt a Framework At a very basic layer, cybersecurity frameworks provide organizations with a starting point from which to structure and develop their security culture and posture. With built-in customization mechanisms (i.e., tiers, profiles, etc.), oftentimes frameworks can be adjusted for use by any type of organization. When it comes to the NIST Cybersecurity Framework specifically, here are a few ways it can help:
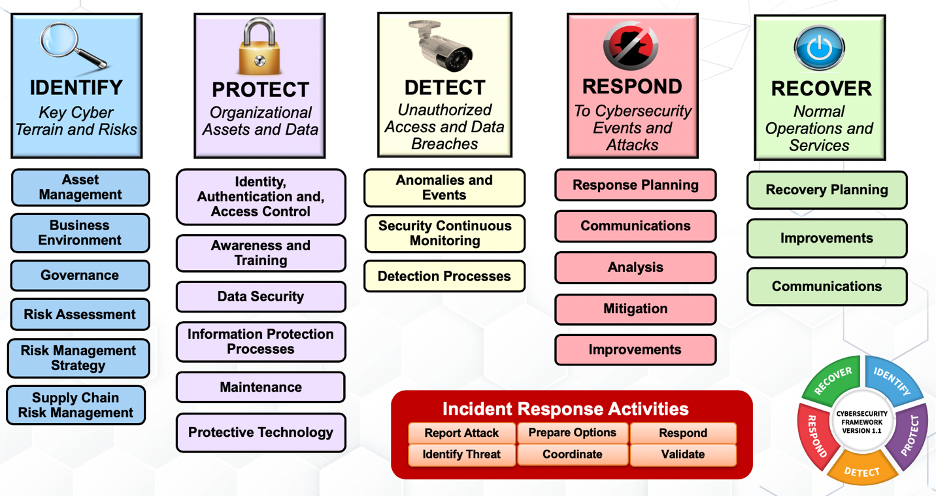
Understanding & Implementing the NIST Cybersecurity Framework While some organizations may simply look to the NIST Cybersecurity Framework as a reference point to improve their cybersecurity posture and strategy (i.e. the Seven Steps for Improving or Developing a Risk-Informed Cybersecurity Program), others may wish to leverage the Framework as more of a comprehensive solution for structuring their teams, delegating workloads, establishing expectations, and driving common dialogue. For the latter, it’s important to first understand the three primary components used to develop a holistic cybersecurity program.
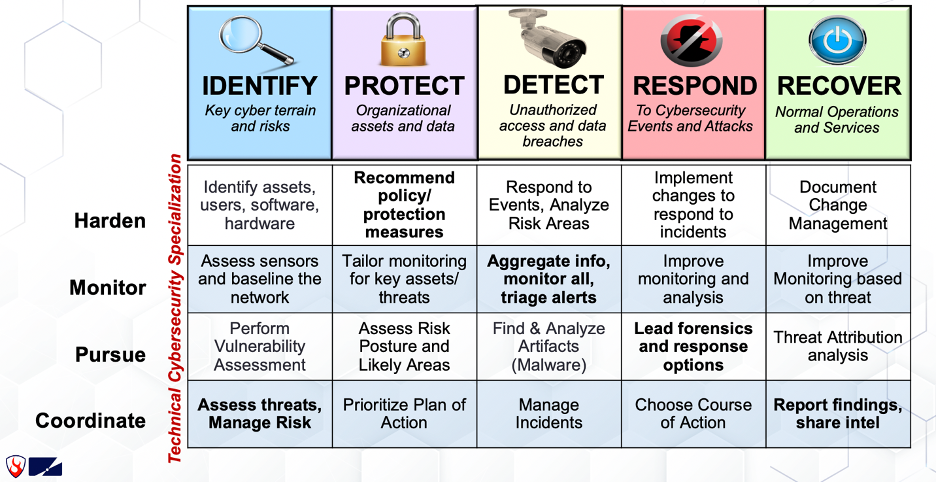
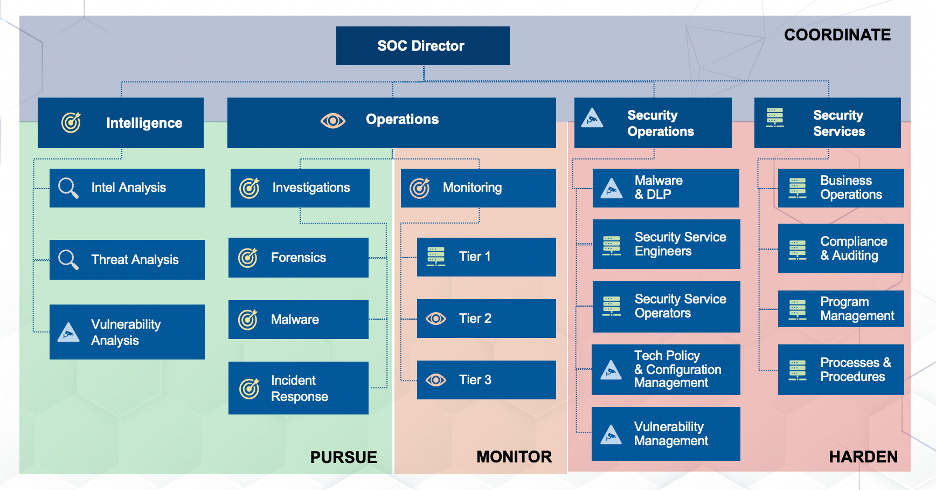
Using these pieces of the Framework, organizations are able to identify and prioritize their business requirements and material risks, and then make reasonable and informed cybersecurity decisions that lead to both feasible and cost-effective improvements. Next, kick off a deeper dive below the rote memorization of its five Core Functions and break the Framework down into more digestible pieces using the Categories. So, what are each of the five Core Functions, and what do (or should) they, do? Once the grouping of outcomes from the Framework’s categories have been grasped, you may find it helpful to apply more technical cybersecurity specializations. As an example, Laura Lee, VP of Cyber Training at By Light Professional IT Services, LLC and Adjunct Professor for Graduate Cybersecurity courses at the University of Colorado, Boulder and National University, takes the following approach: In the figure above, Laura suggests four technical cybersecurity specializations as outlined along the vertical axis of the chart. Individuals charged with executing within the ‘Harden’ specialization, for example, have responsibilities across all five of the Core Functions as defined by the NIST cybersecurity framework and operate by hardening everything across the entire enterprise (i.e. not just Windows devices or systems). To put it all together for “real-world” implementation, Laura applies the NIST Cybersecurity Framework, and the related technical cybersecurity specializations, to the typical structure of a security operations center (SOC) in the figure below. As with other frameworks, the NIST Cybersecurity Framework exists as a template from which organizations can build, grow, transform, or evaluate. Whether you’re looking to capture the current vs. future state of your cybersecurity program, need to analyze your cybersecurity maturity against compliance mandates, or are just starting to build your cybersecurity best practices from scratch, the NIST Cybersecurity Framework encourages efficiency and provides the flexibility and versatility to enable innovation. Note: It’s worth calling out that cybersecurity leaders should also consider their respective, industry-specific frameworks (i.e. HITRUST for healthcare, etc.). To learn more about how you can utilize the NIST Framework to improve your security posture, check out our Governance, Risk, and Compliance Services
Comments are closed.
|
|
© 2020 By Light Professional IT Services LLC. All Rights Reserved.
|

 RSS Feed
RSS Feed
