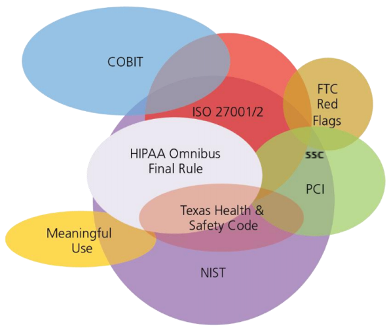
By Fairuz RafiqueThe Healthcare Information Trust Alliance (HITRUST)™ was formed in 2007 with the goal to provide a means for organizations to protect healthcare information in a streamlined and systematic method that was conducive of a successful cybersecurity program. As a result, HITRUST developed the Common Security Framework (CSF)®, for organizations to incorporate a comprehensive risk management framework in environments with complex business and regulatory considerations. It allows organizations that create, access, store, or exchange Protected Health Information (PHI) a means to systematically protect the PHI per multiple industry guidance, directives, laws, regulations, frameworks and standards. HITRUST CSF has a highly successful track record in relevance in the healthcare vertical. The framework is dynamic and has been designed for adoption across multiple industry verticals. To date, the HITRUST CSF has been successfully adopted by numerous industries outside of healthcare and continues to be adopted by diverse organizations. Further, HITRUST continues to scale globally as a major cybersecurity framework, particularly in the Asia Pacific region. (Source) How does it compare to other frameworks? In order for HITRUST CSF to have global applicability, the framework leveraged the well-known ISO/IEC 27001: 2005 and ISO/IEC 27002:2005 standards. In addition, the HITRUST CSF provides comprehensive coverage by incorporating multiple healthcare information security-related regulations, standards, and frameworks such as:
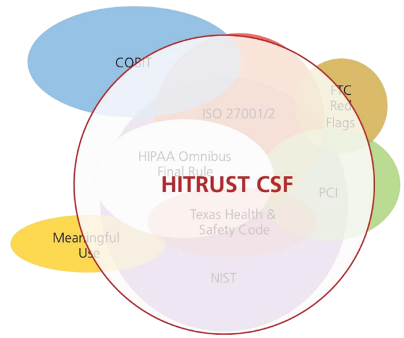
The Department of Homeland Security identifies Healthcare and Public Health as a critical infrastructure sector of the United States, and the United States Department of Health and Human Services (HHS) is tasked by DHS to coordinate critical infrastructure security and resilience activities for the sector. To help provide guidance to agencies, regulators and the private sector, the DHS published the Healthcare Security Cybersecurity Framework Implementation Guidance in which HITRUST CSF is cited as a ‘model’ implementation of the NIST Cyber Security Framework (CSF) (Source). The following diagram provides an overview of the various frameworks, regulations and directives pertinent to the healthcare sector and how the HITRUST CSF attempts to provide a comprehensive risk management framework that addresses the numerous authoritative sources. Who needs HITRUST CSF certification? In any industry vertical, business relies on a list of critical players forming a supply chain. Vendors, contractors, distributors, hospitals, clinics, service providers, and insurance providers are just a few of the players that form a healthcare supply chain. These businesses have numerous needs and business functions that require them to handle sensitive data such as:
If your organization handles any of these types of information, the HITRUST CSF can be leveraged as a means to protect it. Oftentimes, organizations will elect to undergo a HITRUST CSF assessment in hopes of achieving the HITRUST CSF certification. Keep in mind, the HITRUST CSF is a comprehensive framework and the certification process is arduous – organizations with serious needs and serious business implications chooses to undergo the HITRUST CSF certification. A total of four HITRUST CSF assessments are offered, each with its own objective. They are:
Organizations that do not have a mature cybersecurity program are recommended to first perform a readiness assessment. The readiness assessment can be completed by your internal security personnel or trusted cybersecurity partner. The results of the assessment will provide you critical insight into all the gaps you will need to remediate prior to being ready to undergo a validated assessment. How to Prepare Organizations that may be contemplating the HITRUST CSF certification will need to focus on developing and implementing the basic cybersecurity requirements found across frameworks. At a high level, these practices include:
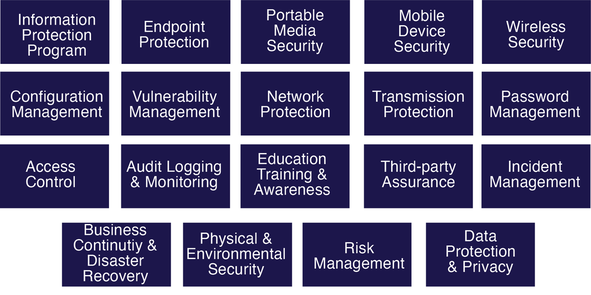
This list above is not all inclusive and readers are advised to seek guidance from previously established frameworks and supporting guidance. A total of 19 control domains establishes the foundation for the HITRUST CSF, and they are illustrated below: During the certification process, auditors/assessors(?) will attempt to uncover deficiencies in control domains, or “control gaps”. In the event that control gaps are identified during the assessment process, your organization will fail to achieve the HITRUST CSF certification as a HITRUST CSF certification is only awarded when controls have deficiencies considered to be “acceptable”. These deficiencies are recorded and categorized into corrective action plans that must have evidence of ongoing improvement.. More about corrective action plans tolerated for awarding a certification will be covered in Part 2 of this blog. Keep in mind that the validated assessment is the only assessment type offered by HITRUST that generates the following:
About EmberSec EmberSec (A By Light Company) is an accredited HITRUST CSF 3PAO and has a track record in being uniquely familiar with the HITRUST CSF process. Our past projects allow us to have an unique perspective with the HITRUST CSF assessment process. We have proven leadership in successfully partnering with clients as their HITRUST CSF 3PAO in performing their validated assessment and annual interim assessment. In each case, our clients were able to successfully:
We will be happy to extend this insightful leadership to your HITRUST CSF certification objectives as you seriously consider on taking your cybersecurity program to the next level. Comments are closed.
|
|
© 2020 By Light Professional IT Services LLC. All Rights Reserved.
|

 RSS Feed
RSS Feed
